White Paper: EMP & IEMI Protection Concepts For Data Centers
Electromagnetic Protection Concepts
About
EMP, or High-Altitude Electromagnetic Pulse (also “HEMP”), along with other electromagnetic threats, such as IEMI (collectively known as “E-Threats”), used to be the domain of the Department of Defense. It has become increasingly apparent that even for national defense purposes, civil infrastructure is critical to the efficient functioning of our national security. Therefore, the identification of critical data centers and applications within data centers bears increasing consideration for HEMP/IEMI mitigation and protection.
This white paper proposes several ideas and options to efficiently deliver HEMP/IEMI shielded data centers without the radical increase in costs over non-shielded facilities.

The Authors
Thomas Blythe Gaven Industries, Inc.
thomas.blythe@gavenindustries.com +1.724.352.8100 ext. 237
Joel Kohler Gaven Industries, Inc
joel.kohler@gavenindustries.com +1.724.352.8100 ext. 214
Davidson A. Scott, P.e.Electromagnetic Associates, LLC
1. Introduction
Data Centers are now a key component to every sector of the economy, including each of the 16 areas identified by DHS as “Critical Infrastructure.” With so much of our day-to-day existence touching data and communications, the continued reliable availability of this critical infrastructure must be assured.
One of the threats to the ubiquitous availability of data and communications infrastructure is electromagnetic threats, including HEMP/EMP and Intentional Electromagnetic Interference, known as “IEMI.” Until recent years, absent any specific requirements, it has not been economically feasible to make every data center “EMP or EMI Resilient,” that is, able to operate before, during, and after a large-scale EMP or EMI event. However, due to decades of experience in shielding, firms such as Gaven Industries have developed techniques and methods to mitigate costs.
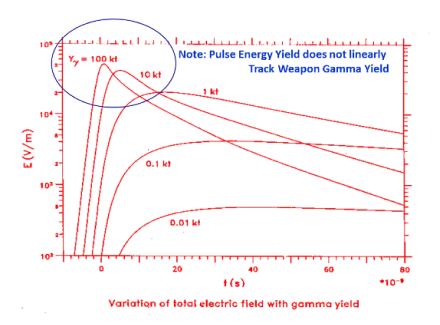
For those who have not been made aware of HEMP/IEMI or other electromagnetic threats, a HEMP event occurs when a bad actor detonates a nuclear weapon at an altitude (usually above 20 miles in altitude. There are several different phases of a HEMP event known as “E-1, E-2, and E-3 transients.” This paper emphasizes the threat from “E-1,” a broad-spectrum high-energy electromagnetic energy pulse generated when gamma rays from a nuclear detonation interact with the atmosphere, creating a potentially dangerous condition to unprotected electronics or other systems. While the area of the Earth affected is largely dependent upon the height of the nuclear detonation, the energies experienced are not closely correlated with the size of the nuclear device and are remarkably consistent.
Intentional Electromagnetic Interference or “IEMI” is a class of electromagnetic threat that can damage, degrade, or disrupt communications, electronics, or other critical systems. This paper focuses primarily on avoiding “damage” to systems, but risks of degradation and disruption are also essential and are reduced when system damage is mitigated. IEMI weapons and ensuing threats vary significantly from one to another. One common thread is that these attacks are often conducted at a relatively close distance using pulse equipment typically hand carried or driven to the attack point.
While the generation of HEMP/EMP was associated with the detonation of nuclear devices early in the development of nuclear weapons, it wasn’t well understood until the nuclear test “Starfish Prime” conducted by the United States and the detonation of “Tsar Bomba” in the USSR in the early 1960s. These effects were largely classified until the early 1980s, when articles reached mainstream news reports. In the United States, Conrad Longmire was pivotal in developing the understanding of the physics of HEMP. The resulting appreciation for HEMP was vital in developing techniques for mitigating the threat and protecting the country’s critical assets.
The US Military released “MIL-STD 188-125-1 and MIL-STD 188-125-2,” which were unclassified specifications for HEMP protection in the early 1990s. These have been the basis for protecting “Time Urgent” military facilities ever since.
2. Electromagnetic Shielding
The fundamental way to protect against electromagnetic threats is to use established engineering principles, whether EMP or EMI, to exclude harmful energy from vulnerable systems while simultaneously allowing those systems to operate as intended. Often, this requires the placement of conductive shielding, sometimes referred to as a “Faraday Cage.” It is important to note that all EMP shields are Faraday Cages; however, not all Faraday Cages provide EMP protections.
Harmful energy manifests itself in “Electric Fields” as well as “Magnetic Fields,” which comprise “electromagnetic fields.” The HEMP threat is described in the MIL-STD as mostly “Magnetic” in nature at frequencies from 10MHz to 10kHz, and mostly “Electric” in nature at frequencies from 10MHz to 1000MHz. Electromagnetic Shielding must reduce electric field levels by 10,000 times to ensure the uninterrupted operation of modern electrical and electronic systems. Also, a means to access, support, and communicate with systems inside a shielded area must be integrated into an operational shield. These requirements are core considerations in designing and developing sustainable protective solutions.
The established method for mitigating the E-threat begins with a completely enclosed, RF-shielded volume. In the case of most applications, this would be for all walls, floors, and ceilings to be integrated into a conductive barrier – the so-called “6-sided box.” Shielded volumes can range from small-scale, such as a shielded IT cabinet, to very large facilities, utilizing prefabricated wall, ceiling, and flooring panels that are joined together on-site. Shielded solutions may be fixed in place, transportable, or mobile – designed and constructed to satisfy the operational requirements of end users and other applicable performance criteria.
Throughout the consultation and design process, companies that offer E-threat shielding consultation, like Gaven Industries, will work with architectural and engineering disciplines to identify and recommend waveguide requirements for the enclosure or facility.
Michael Faraday, in 1836, described an enclosure formed from continuously conductive elements that excluded electric fields from the interior of the “cage.” This description is commonly called a “Faraday Cage” and forms the basis of a functional E-threat shield. However, at lower HEMP frequencies, where energy is primarily magnetic in nature, it is necessary to expand upon the Faraday cage concept. For this reason, E-threat shielded solutions are most conveniently made from ferromagnetic materials such as steel which simultaneously creates a functional electrical field shield (Faraday cage) and a magnetic shield. Electric/magnetic shields can be made with other materials, but non-ferromagnetic shields must be thicker to achieve the full performance envelope of an EMP - (10kHz - 1GHz).

Figure 3: RF shielding waveguide point-of-entry protections (Gaven)
Waveguides are integrated into shielded enclosure designs to facilitate the movement of air, water, fuel, fiber-optic cabling, and other support elements to pass from outside the shield to the interior of the shield or vice versa without compromising the integrity of the shield. These follow particular electromagnetic principles that depend upon the material passing through the waveguide and the dimensions of the waveguide.
Specifically, a waveguide seeks to create an electromagnetic “cut-off” condition – where the energy on one side of a waveguide cannot travel through to the other side. When properly engineered, this allows, as an example, air for ventilation to pass through a shielded wall without compromising its requirements for shielding against electromagnetic energy, such as that contained in an IEMI attack or HEMP event.
When these pass-throughs are installed in interlocked pairs, it provides the means to obtain access to a shielded enclosure without compromising the integrity of the shield by opening a single door. Commonly, access hatches must also be part of a shield for maintenance and operational purposes. These all follow similar principles to exclude electromagnetic energy.
More often than not, shielded enclosures need to be connected to a power source. As such, conductors required to facilitate power and control signals must pass through the shield. However, once a conductive cable passes through a shield, it compromises the shielding significantly because Ethreat energy couples to cables and travels through the shielding, where it will “reradiate,” allowing harmful energy inside a protected area. Previously described conditions can be avoided by appropriately selecting passive points of entry where copper conductors pass through electrical filters before entering the shielded volume. Most often, this requires using a “Low-Pass Filter,” which uses capacitors and inductors to create a condition where, for instance, 60Hz power can pass through the shield. Still, HEMP and IEMI energy, which is much higher in frequency, cannot pass without being significantly reduced in magnitude. These are readily available for many different applications by commercial vendors. When this is the case, an experienced E-threat consultant is key to success planning for EMP and IEMI protection.

Figure 4: HEMP-shielding door inside Gaven Modular Enclosure Structure
Shielded facilities that require people to work in the protected space must have a means of access. Special shielded doors that, when closed, exclude E-threat energy have been designed, fielded, and qualified.
When these pass-throughs are installed in interlocked pairs, it provides the means to obtain access to a shielded enclosure without compromising the integrity of the shield by opening a single door. Commonly, access hatches must also be part of a shield for maintenance and operational purposes. These all follow similar principles to exclude electromagnetic energy.
3. Data Center EMP Resilience
Data Centers are unique facilities that rely more heavily on large and redundant power densities and effective large-capacity cooling than many other types of facilities. They also rely on large, redundant data pipes in short and long-haul configurations. Both power and cooling have solutions and options within the E-threat shielding design space. Gaven Industries has developed unique solutions that provide both cost and schedule benefits and open the possibility of capital-efficient construction and retrofit of new and existing data centers that may have reached technical end-of-life scenarios. Recently, Gaven retrofitted an existing facility with a 10,000 sq-ft shield via prefabricated panels for a combination data center and operations center. In addition to the shielded volume, Gaven provided HEMP shielding for backup power generators. As a part of this scope, Gaven provided complete BIM coordination for the effort along with MIL-STD 188- 125 acceptance testing.
In another recent project, Gaven installed a 30,000+ sq-ft shield that included a private data center environment. This shield also utilized a prefabricated panel design. In addition to the shielded volume, Gaven provided and tested dozens of HEMP protected power line filters along with BIM coordination and acceptance testing.
On a smaller scale, Gaven Industries offers standard and custom RF and HEMP-shielded data racks and cabinets. This means that data center providers can shield smaller than room-size portions of their data centers quickly and efficiently.
EMP resilience for the data center is another option, like redundancy, that can be monetized for data center providers. The reality is that more than redundancy is needed to protect critical data. An EMP-resilient solution offers tangible value to end users with time critical services and operations.
Power for E-threat-protected data centers has the same requirements as non-shielded data centers. However, the main difference is that E-threatprotected power and backup power must be EMP shielded and filtered. New technologies allow power feeds into shielded data centers to be provided at medium voltages. This dramatically simplifies Ethreat-protected power feeds and lowers costs over (until recently) traditional grid-attachment methods. Gaven Industries can provide guidance on these newer methods of power grid attachment at medium voltages in shielded facilities.
Additionally, for backup power, generator sets configured similarly to existing unshielded facilities can be utilized in E-threat protection applications. Protected generator sets are integrated into an Ethreat-protected enclosure utilizing the same principles for E-threat mitigation described throughout this document. New technologies developed by Gaven and its partners can be applied for cost-effective solutions.
Data Center cooling is greatly dependent upon moving air to support heat rejection. E-threat shielding performance requires that this air be moved through waveguides that support the blocking of electromagnetic energy. Gaven and Gaven’s partners have developed strategies using absorptive materials (some of which can be integrated into concrete mixes) and labyrinthine air passageways that can support large air volumes more efficiently than traditional HEMP waveguides. This cooling approach also applies to backup generation systems which also require large volumes of air for heat rejection.
Shielding for a data center can be implemented as the entire facility envelope, a portion of the data center, or scaling to meet specific client needs. The desired size of the facility and other building objectives will typically dictate the shield construct approach most appropriate for a given application. For example, an entire facility may be constructed using prefabricated metal panels, which satisfies the need for E-threat protection as well as form the structure and overall envelope of the building.
Alternatively, the building or host facility may be constructed using conventional methods and materials where the E-threat shield is assembled within the building envelope.
Another method for protecting a data center’s critical assets from E-threat is to utilize modular, containerized enclosures. These enclosures may be fabricated to specification offsite and installed when a customer requires a shielded space. This option allows for a “hybrid” facility where standard operating data centers can expand their capabilities and offer E-threat-protected space without significant costs.
It is also possible to host individual containers at customer sites for migration or for continuity of operations purposes. This method may also be appropriate for the retrofit of existing data centers. Shielding smaller-scale volumes is another approach, either at the rack level or cage level, as previously discussed.
However, this is somewhat offset by the fact that IEMI threats can have repeating waveforms that subject “victim” systems to multiple energy pulses rather than a single HEMP pulse.
4. Data Center Communications E-Threat Resilience
Data communications must also be E-threat resilient in a properly protected shielded enclosure. Fiber Optic repeater (“Regen”) stations must be placed at approximately 50 to 100-mile intervals. Bandwidth breakout points may be required much more frequently.
Each of these “nodes” must also implement EMP shielding if an E-threat-shielded data center is to remain functional; otherwise, there is a significant risk that the data center will not remain operational and become “islanded” such that it cannot communicate with the outside world.
Gaven Industries and its partners have developed options for regen and breakout sites that provide Ethreat resilience to fiber optic communication nodes.
5. Comments About IEMI
Intentional Electromagnetic Interference, IEMI, is related to HEMP, and solutions can be similar; however, IEMI is generally present over a higher frequency spectrum than HEMP. This means that HEMP remediation can also be modified to include IEMI E-Threats. Since IEMI is generally a higher frequency E-threat, there are some remediation measures that can be applied that do not generally apply to the lower-frequency portion of the HEMP threat. This includes undergrounding of penetrations so that energy is absorbed through more passive means. Also, since IEMI is a localized E-Threat, there can be a trade-off of physical security for electromagnetic shielding for IEMI because, unlike HEMP, IEMI is subject to the “inverse square law” and Free-Space Path Loss where field levels rapidly decay with distance and with increasing frequency
However, this is somewhat offset by the fact that IEMI threats can have repeating waveforms that subject “victim” systems to multiple energy pulses rather than a single HEMP pulse.
6. Conclusion
New approaches are available to hosting providers and data center planners to shield entire data centers and data center critical assets. Electromagnetic Threats are not expected to go away. It is a matter of time before E-threat protection is required for many, if not all, Critical Infrastructure areas. Shielded data centers will undoubtedly be an essential component of E-threat resilience. Gaven Industries is at the forefront of designing and furnishing E-threat solutions that are cost-effective, reliable, and sustainable.
White Paper: EMP & IEMI Protection Concepts For Data Centers

















About Us
Gaven Industries specializes in EMI, EMP, HEMP, and RF shielding solutions, including expertly crafted doors, shielded structures, rooms, and data racks.

Quick Links
Stay Informed
Subscribe for exclusive updates
and insights from Gaven Industries.
Copyright © 2024 Gaven Industries Inc. All Rights Reserved.
